When deploying SFTP one must consider the authentication methods one intends to use. There are many authentication methods but most implementations focus on basic authentication (username/password) or public key authentication. For the purposes of this writing we will make use of both. Sentry provides the ability to make this process seamless and easy. We will show the following scenarios since Sentry is intended to sit between an SFTP client and an SFTP server:
1. Basic Authentication to Basic Authentication
2. Basic Authentication to Public Key Authentication
3. Public Key Authentication to Public Key Authentication
4. Public Key Authentication to Basic Authentication
With these scenarios we see that Sentry already provides lots of flexibility to accomplish the needs of just about all implementations one might desire to put in place.
First we would like to mention that Sentry comes with SFTP ready to go. We need to create the following policies while keeping in mind the authentication method we need to implement:
A. Basic Authentication:
For the purposes of this article we will setup an LDAP policy for end-users connecting to Sentry via SFTP and username/password for Sentry connecting via SFTP to the back-end SFTP server.
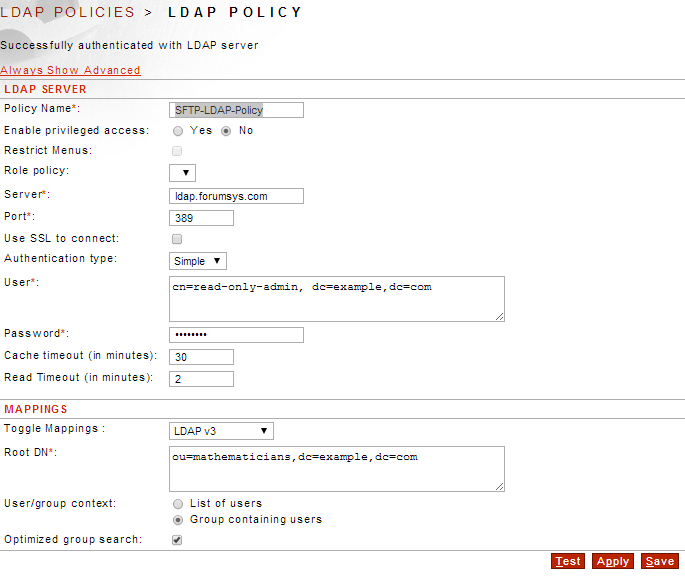
a. LDAP Policy:
Access--->User Policies--->LDAP
. Click New
. Fill in the information mainly the following
- Policy Name: Forum-LDAP-Server
- Enable Privilege Access: No
- Server: ldap.forumsys.com
- User: cn=read-only-admin,dc=example,dc=com
- Password: password
- Root DN: ou=mathematicians,dc=example,dc=com
- User/group context: Group containing users
. Click Apply
. Click Test to see if we can connect to the LDAP successfully. You will see the result at the top of the screen.
. If success click Save.
b. Username/Password (for the back-end SFTP Server):
Get an authorized account information that has SFTP privileges on the SFTP Server.
B. Create the SFTP Content Policy:
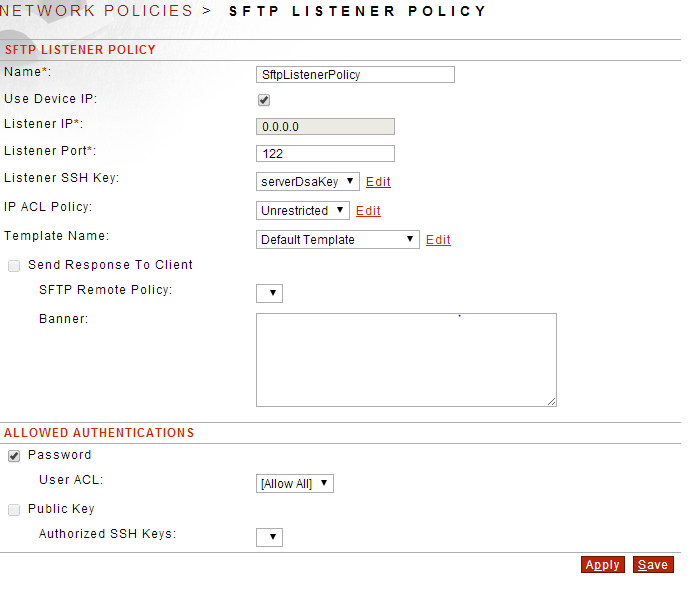
a. Create a SFTP Listener Policy:
Gateway--->Network Policies--->Network Policies
- Click New
- Select SFTP and Click Next
- Select Listener and Click Next
- Fill in the following info:
- Name*:
- Use Device IP:
- Listener IP*:
- Listener Port*:
- Check Password for Allowed Authentications
- Click Apply and Save
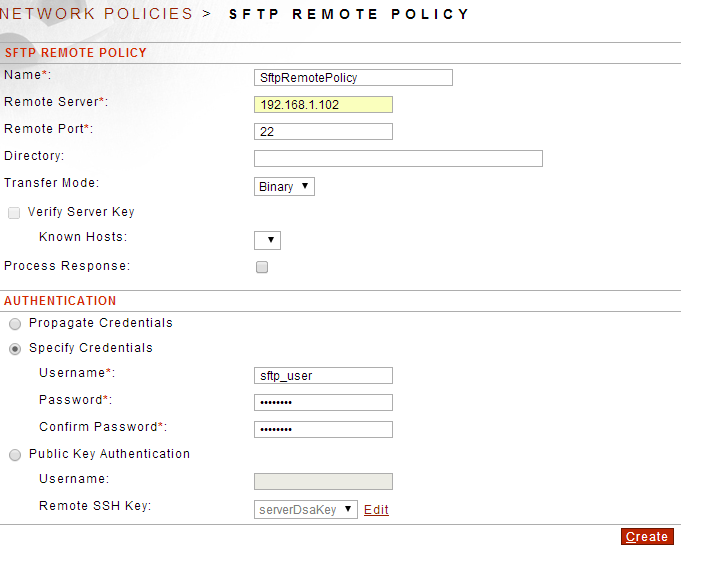
b. Create a SFTP Remote Policy:
Gateway--->Network Policies--->Network Policies
- Click New
- Select SFTP and Click Next
- Select Remote and Click Next
- Fill in the following info for the Back-end SFTP Server:
- Name*:
- Remote Server*:
- Remote Port*:
- Select Specify Credentials and fill in the username/password of the SFTP account on the back-end server.
-
c. Create Content Policy:
Gateway--->Content Policies--->XML Policies (or HTML Policies)
- Click New
- Name it and click Next
- Select your SFTP Listener and Remote Policies:
- Listener Policy:
- Remote Policy:

You are now ready to SFTP:
The Client used in this exercise is PSFTP and the back-end Server is BitVise SSH Server.
The -P, in the command below, is for the port number. You do not have to setup the normal SFTP port, you can listen on any available port, in this case 122. Also, the user is an LDAP user that will connect to Sentry first and then Sentry will connect to the back-end server with the credentials provided by that server's administrator:
$ ./psftp -P 122 euclid@192.168.1.107
Connecting for the first time, the PSFTP client will need to agree to save the key supplied by the server so that it knows the server for future connections. This key is called Known Host Key.
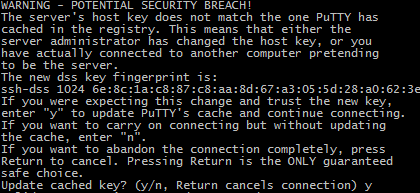
euclid@192.168.1.107's password: password
psftp> ls
Listing directory ./.
p--------- 1 0 0 127970 Jun 08 12:15 Less_than_1M_DOC.docx
p--------- 1 0 0 282840 Jun 08 12:15 Less_than_1M_EXE.exe
p--------- 1 0 0 47156 Jun 08 12:15 Less_than_1M_JPEG.jpg
p--------- 1 0 0 671062 Jun 08 12:15 Less_than_1M_PDF.pdf
p--------- 1 0 0 156582 Jun 08 12:15 Less_than_1M_TXT.txt
p--------- 1 0 0 6132775 Jun 08 12:15 More_than_1M_DOC.docx
p--------- 1 0 0 1331024 Jun 08 12:15 More_than_1M_EXE.exe
p--------- 1 0 0 7432880 Jun 08 12:15 More_than_1M_PDF.pdf
p--------- 1 0 0 4057328 Jun 08 12:15 More_than_1M_TXT.txt
p--------- 1 0 0 28824 Jun 08 12:15 SwA_XML_to_SFTP.fsg
psftp> put test.txt
local:test.txt => remote:./test.txt
psftp> ls
Listing directory ./.
p--------- 1 0 0 127970 Jun 08 12:15 Less_than_1M_DOC.docx
p--------- 1 0 0 282840 Jun 08 12:15 Less_than_1M_EXE.exe
p--------- 1 0 0 47156 Jun 08 12:15 Less_than_1M_JPEG.jpg
p--------- 1 0 0 671062 Jun 08 12:15 Less_than_1M_PDF.pdf
p--------- 1 0 0 156582 Jun 08 12:15 Less_than_1M_TXT.txt
p--------- 1 0 0 6132775 Jun 08 12:15 More_than_1M_DOC.docx
p--------- 1 0 0 1331024 Jun 08 12:15 More_than_1M_EXE.exe
p--------- 1 0 0 7432880 Jun 08 12:15 More_than_1M_PDF.pdf
p--------- 1 0 0 4057328 Jun 08 12:15 More_than_1M_TXT.txt
p--------- 1 0 0 28824 Jun 08 12:15 SwA_XML_to_SFTP.fsg
p--------- 1 0 0 15 Jun 15 09:50 test.txt
psftp> get Less_than_1M_DOC.docx
remote:./Less_than_1M_DOC.docx => local:Less_than_1M_DOC.docx
psftp> ls
Listing directory ./.
p--------- 1 0 0 127970 Jun 08 12:15 Less_than_1M_DOC.docx
p--------- 1 0 0 282840 Jun 08 12:15 Less_than_1M_EXE.exe
p--------- 1 0 0 47156 Jun 08 12:15 Less_than_1M_JPEG.jpg
p--------- 1 0 0 671062 Jun 08 12:15 Less_than_1M_PDF.pdf
p--------- 1 0 0 156582 Jun 08 12:15 Less_than_1M_TXT.txt
p--------- 1 0 0 6132775 Jun 08 12:15 More_than_1M_DOC.docx
p--------- 1 0 0 1331024 Jun 08 12:15 More_than_1M_EXE.exe
p--------- 1 0 0 7432880 Jun 08 12:15 More_than_1M_PDF.pdf
p--------- 1 0 0 4057328 Jun 08 12:15 More_than_1M_TXT.txt
p--------- 1 0 0 28824 Jun 08 12:15 SwA_XML_to_SFTP.fsg
p--------- 1 0 0 15 Jun 15 09:50 test.txt
psftp> rm test.txt
rm ./test.txt: OK
psftp> ls
Listing directory ./.
p--------- 1 0 0 127970 Jun 08 12:15 Less_than_1M_DOC.docx
p--------- 1 0 0 282840 Jun 08 12:15 Less_than_1M_EXE.exe
p--------- 1 0 0 47156 Jun 08 12:15 Less_than_1M_JPEG.jpg
p--------- 1 0 0 671062 Jun 08 12:15 Less_than_1M_PDF.pdf
p--------- 1 0 0 156582 Jun 08 12:15 Less_than_1M_TXT.txt
p--------- 1 0 0 6132775 Jun 08 12:15 More_than_1M_DOC.docx
p--------- 1 0 0 1331024 Jun 08 12:15 More_than_1M_EXE.exe
p--------- 1 0 0 7432880 Jun 08 12:15 More_than_1M_PDF.pdf
p--------- 1 0 0 4057328 Jun 08 12:15 More_than_1M_TXT.txt
p--------- 1 0 0 28824 Jun 08 12:15 SwA_XML_to_SFTP.fsg
psftp>
psftp> exit
Using username "euclid".
$ ls Less_than_1M_DOC.docx
Less_than_1M_DOC.docx
This concludes the SFTP setup where Basic Authentication is used end-to-end via Sentry.
C. Basic Authentication to Public Key Authentication
In the first exercise above we have setup Basic Authentication incoming into Sentry and the same outgoing to the back-end SFTP Server.
In this exercise we will only need to setup Public Key Authentication from Sentry to Back-end SFTP Server.
Public Key Authentication is where keys are used for the purposes of authentication and encryption. The client maintains the private and public key pair while the server is supplied with the same public key. Keys normally are created on the client but they don’t have to. In our case here we will use Sentry to create the SSH key pair and supply the public key to the Back-end SFTP Server.
. Create SSH key pair
. Download the public key and distribute to the Back-end SFTP Server
i. Create the SSH Key pair:
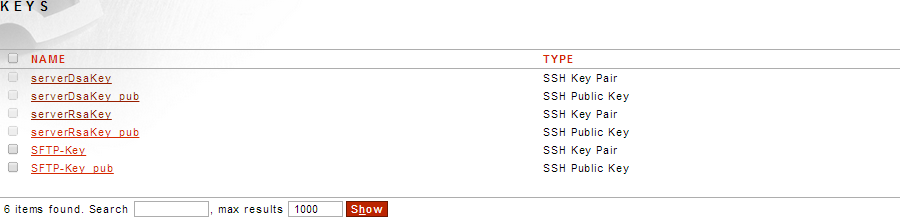
Go to Resources--->PKI--->Keys
Click New
Select OpenSSH Key Pair and Click Next and fill in the following info:
- Name*:
- Algorithm:
- Key Size (in bits):
- Passphrase:
Note: You can leave the Passphrase blank, but if you choose to use a Passphrase then you will need to supply it even when doing Public Key Authentication.

ii. Download the public key and send to the Back-end SFTP Server:
Go to Resources--->PKI--->Keys
Click on the public key and Click OpenSSH hyperlink to download:
Download: OpenSSH
Transfer the Key to Back-end Server and place it where this Server saves the public keys
iii. Configure Sentry to use public key authentication to the Remote SFTP Server:
(This is a one-step change to the Remote SFTP Policy)
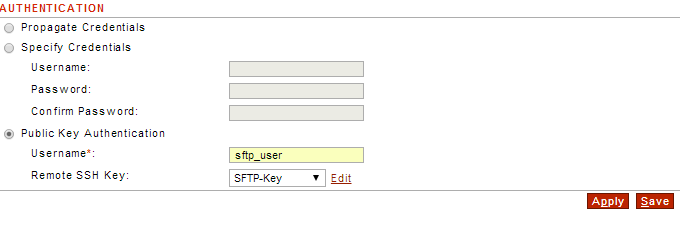
. Go to Gateway--->Network Policies and click to open you SFTP Remote Policy
. In the Authentication section select Public Key Authentication, enter the SFTP user to the Back-end SFTP Server and select the key to use:
Confirm Password:
- Public Key Authentication
- Username*:
- Remote SSH Key:
Apply and Save
You are now ready to use Basic Authentication to Sentry and Sentry in turn will use Public Key Authentication to the Back-end SFTP Server.
$ ./psftp -P 122 euclid@192.168.1.107
euclid@192.168.1.107's password: password
psftp> ls
Listing directory ./.
p--------- 1 0 0 127970 Jun 08 12:15 Less_than_1M_DOC.docx
p--------- 1 0 0 282840 Jun 08 12:15 Less_than_1M_EXE.exe
p--------- 1 0 0 47156 Jun 08 12:15 Less_than_1M_JPEG.jpg
p--------- 1 0 0 671062 Jun 08 12:15 Less_than_1M_PDF.pdf
p--------- 1 0 0 156582 Jun 08 12:15 Less_than_1M_TXT.txt
p--------- 1 0 0 6132775 Jun 08 12:15 More_than_1M_DOC.docx
p--------- 1 0 0 1331024 Jun 08 12:15 More_than_1M_EXE.exe
p--------- 1 0 0 7432880 Jun 08 12:15 More_than_1M_PDF.pdf
p--------- 1 0 0 4057328 Jun 08 12:15 More_than_1M_TXT.txt
p--------- 1 0 0 28824 Jun 08 12:15 SwA_XML_to_SFTP.fsg
psftp>
From the System Log on Sentry you can see that the end user authenticates to LDAP while Sentry uses Public Key Authentication to the Back-end Server:
11:07:23.439 Received SSH password authentication request for 'euclid' on/192.168.1.107:58311
11:07:23.439 Authenticating using 'Local users login module'
11:07:23.439 User 'euclid' not found.
11:07:23.439 Authenticating using 'LDAP login module'
11:07:23.439 Found user 'euclid' in cache for LDAP policy 'SFTP-LDAP-Policy'.
11:07:23.439 Succeeded to authenticate user 'euclid' using LDAP policy 'SFTP-LDAP-Policy'
11:07:23.439 ACL check skipped - no ACL associated with network policy
11:07:23.440 Document entered Communications Layer
11:07:23.440 Handling command 'login'
11:07:23.440 Request document:
11:07:23.440 No TaskListGroup configured, document will not be processed
11:07:23.440 No TaskListGroup configured, document will not be processed
11:07:23.441 Sending remote server a processed request:
Method: POST
Remote...
11:07:23.460 Connecting to SFTP server at 192.168.1.102:22
11:07:23.460 Opening SFTP connection to 192.168.1.102:22
11:07:23.595 Authenticating user 'sftp_user' to 192.168.1.102:22 using publickey method

0 Comments