This is a continuation of the first tutorial (https:// helpdesk.forumsys.com/entries/76439167) where we covered the first two scenarios below:
1. Basic Authentication to Basic Authentication
2. Basic Authentication to Public Key Authentication
The remaining two scenarios are:
3. Public Key Authentication to Public Key Authentication
4. Public Key Authentication to Basic Authentication
In this tutorial we will implement the third scenario. The fourth scenario can be deduced from the first three and is left as an exercise.
D. Public Key Authentication to Public Key Authentication
This is where Public Key Authentication is used end-to-end. Normally, the SSH Key Pair (Private and Public Keys) are generated by the client. The client maintains both the Private and Public keys while distributing the Public Key to the SFTP Server one intends to connect to.
i. Generating the Keys:
There are many key generating tools out there. For our purposes here I will be using puttygen to generate the SSH Key Pair and then export the Public Key so that it can be imported into Sentry.
First launch puttygen:
By default the “Type of key to generate” should already be set to SSH-2 RSA. This is preferable.
Click Generate and follow the instructions. The first thing you will do is move the mouse around the surface provided. The image below shows the generated key:
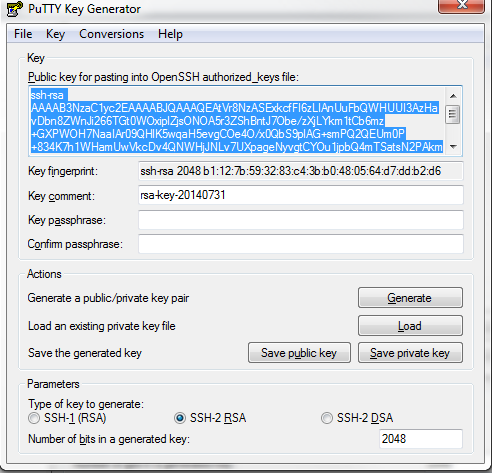
Next you will need to Save the keys by clicking on the 2 Save buttons shown in the image. You will need to save these keys somewhere on your system and give them meaningful names. You will probably want to use names to indicate the sort of use case they would be used for. As an example, here are my key names:
SFTP_PRV_KEY_UseCase1.ppk
SFTP_PUB_KEY_UseCase1
ii. Importing the Public Key to Sentry:
Login to Sentry Web Admin and follow the steps below:
. Go to Resources--->PKI--->Keys:
. Click Import and Select SSH Public Key
. Click Next and Select File upload
. Click Next, add a name for the key then browse to select the public key
. Click Submit

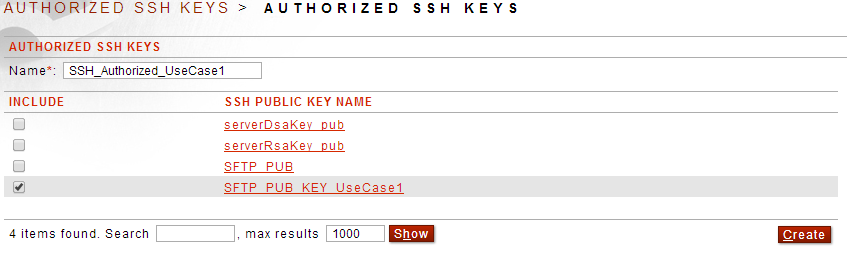
Next you will need to create an Authorized SSH Keys list where you add the newly imported public key:
. Click Authorized SSH Keys under Resources--->PKI
. Click New
. Add a name for this list and then select the public key then click Create
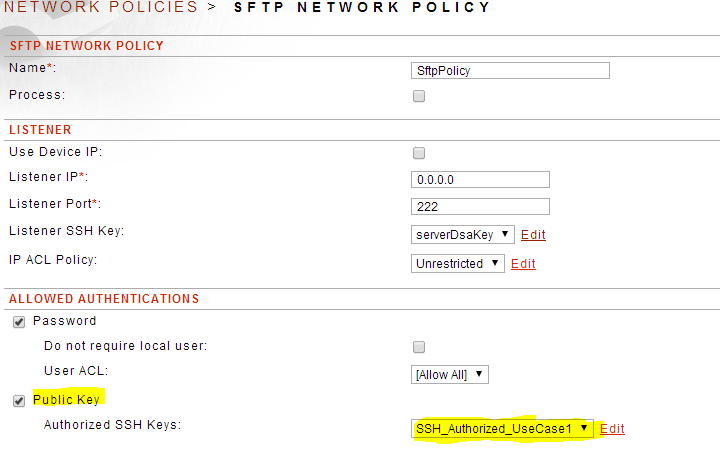
You will now need to go back to your SFTP Proxy Policy, specify Public Key and select the Authorized Key list created above:
iii. Public Key Authentication on the back-end (Sentry to back-end SFTP Server)
. Go to Resources--->PKI
. Click New
. Select OpenSSH Key Pair and click Next
. Add a name and select the Algorithm and Key Size then click Create
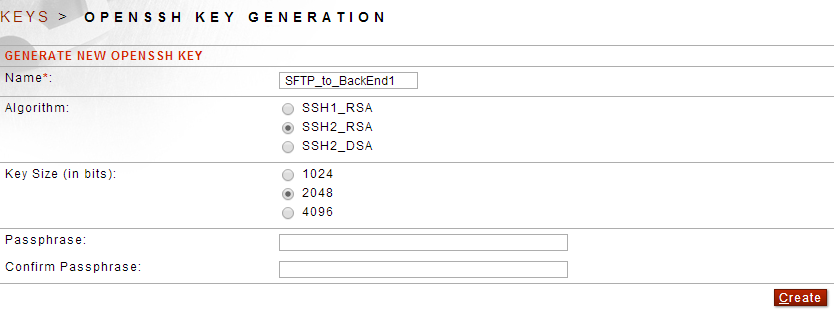
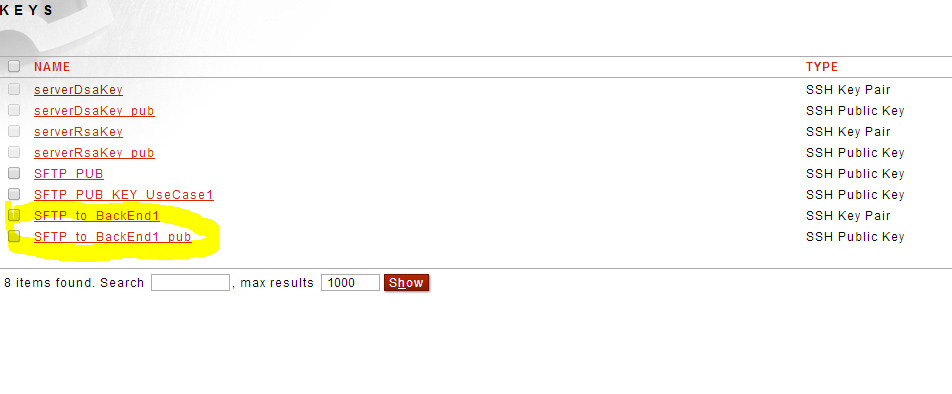
Once created you should see:
You will now need to go back to your SFTP Proxy policy and specify Public key Authentication and select the new key in the drop down as well as the username associated with the key for the Remote Authentication as shown below:
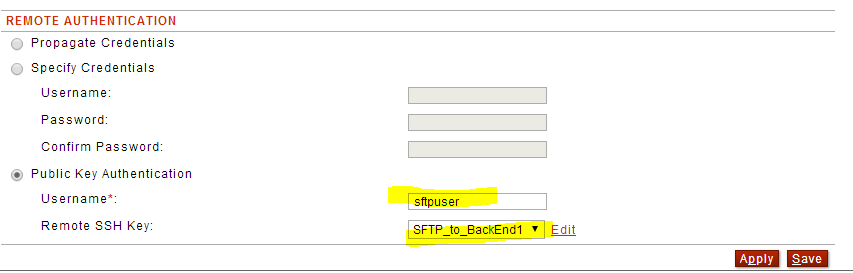
Note: The username above is the actual username on the back-end SFTP Server that the key will be associated with. This username is supplied by the back-end SFTP Server Admin.
Lastly, you will need to export the public key that will be imported by the back-end SFTP Server as an authorized key:
. Go to Resources--->PKI
. Click to open the public key and then Download:
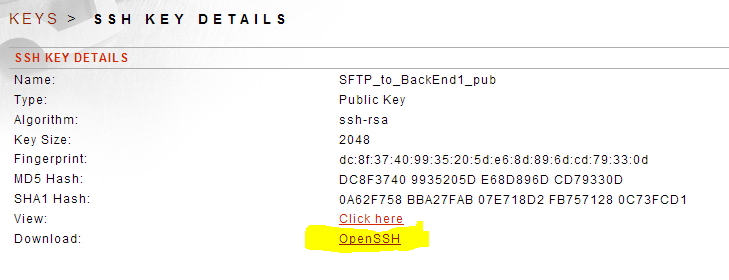
This should download a copy of the public key for distribution to the back-end server.
Below are the log entries showing the connection through Sentry using Public key Authentication:
000334 12:51:57.418 X0001B7 4C057 D Received SSH public key authentication request from
'/10.5.1.192:55782' for 'sftpuser'
000335 12:51:57.418 X0001B7 4C05C D SSH public key authentication valid for user 'sftpuser'
using SSH key 'SFTP_PUB_KEY_UseCase1' [/10.5.1.192:55782]
000336 12:51:57.662 X0000000 4C247 D Connecting to SFTP server at 10.5.1.192:22
000337 12:51:57.707 X0000000 4C054 D Authenticating user 'sftpuser' to 10.5.1.192:22 using
publickey method
As you can see from the log first Public Key Authentication takes place from the end-user to Sentry and then from Sentry to the back-end SFTP Server.

0 Comments