TCPDUMP is used to step through network communication between 2 systems. This is very useful when debugging either communication issues or inspecting data being transferred between the two ends of a connection.
Forum Sentry hardware and virtual appliances do come supplied with TCPDUMP; while software versions rely on TCPDUMP or other packet capturing tools installed on the host. On the appliances packet capturing is invoked under Diagnostics-->Logging-->Packet Captures.

To initiate a TCPDUMP click the Start button. This will launch the tool and capture all traffic on the system. This is called running in Promiscuous Mode. It is best to use filtering to only capture the traffic that pertains to a specific issue. This is done by adding a filter expression before clicking Start.
Examples of filter expression that can be used are:
1. “port 443” to capture traffic on port 443. This is very useful for troubleshooting SSL Handshake issues. Reviewing the capture and following the stream provides insight into where the problem might be. There are usually errors pointing to the problem. Such problems are the wrong certificates being sent by one side or the other. The capture will show the certificates being sent between the two systems. A very common SSL handshake issue that can be diagnosed via packet capture review is the wrong SSL/TLS version being accepted or used by one side or the other.

2. The above example with “port 443” for the filter expression will generate all traffic to port 443, but there may be many network policies utilizing port 443. In this case, make the filter expression more specific by including the host as well. For instance: port 443 and host 10.10.10.10. This filter will only capture traffic between the host Sentry instance and 10.10.10.10:443.

Once a request or a number of requests has been sent to reproduce the issue, click Stop to write a pcap file that can be opened by compatible tools such as Wireshark.
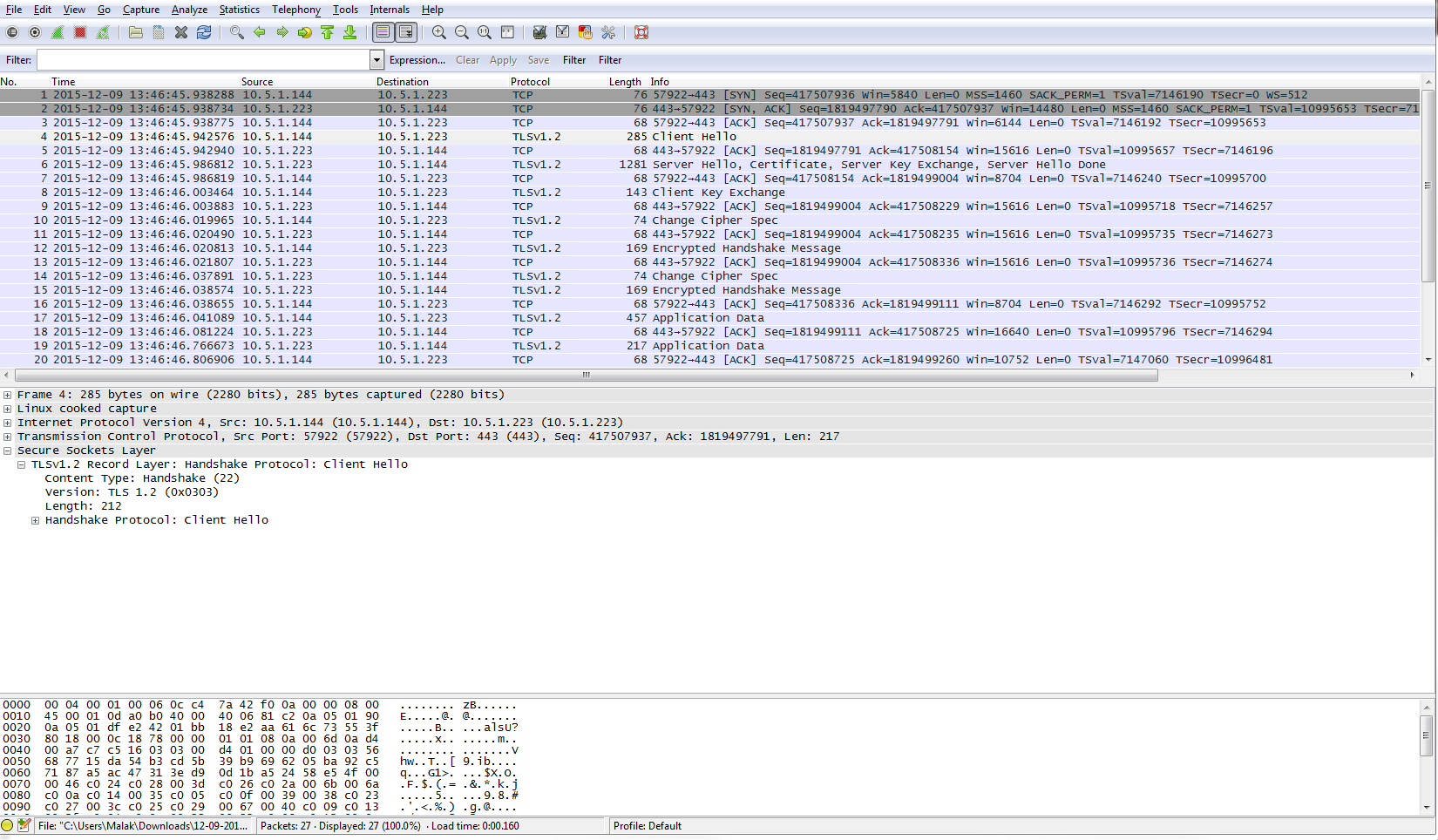
Below is the resulting packet capture when using the filter “host 10.5.1.223 and port 443”. This only captures traffic to the specified IP and Port:
3. The above 2 examples take into account that the remote IP as well as the port associated with that remote policy. To capture traffic from a client, use the Sentry listener policy port as the source port of the client is not known.
Finally, a couple of things to note:
a. When clicking Stop to end the TCPDUMP session, it may be necessary to click the link Diagnostics-->Logging-->Packet Captures to get the entire capture file. This is because often times the file might still be open to write final packets.
b. Experiment with other filter expressions but generally the only 2 needed are a Port and the Client or Remote IP Address.

0 Comments