Introduction
Forum Sentry v8.7 provides a secure, built-in integration for Amazon S3 cloud storage.
In this article, we show how to configure Sentry as a gateway for the S3 storage API. A sample Sentry policy is included with instructions for testing.
As an API Security Gateway, Forum Sentry is uniquely able to implement the following identity management and data privacy requirements for the Amazon S3 cloud storage:
1. Secure TLS Connectivity - Ensure the connectivity across all hops uses the most secure TLS protocols and cipher suites available. This includes tightening the connections between the clients and Sentry as well as Sentry and S3.
2. Local User Authentication - Require a specific set of user credentials managed by your own organization (separate from the AWS credentials).
3. Secure storage of the AWS S3 credentials - The AWS credentials (Access Key ID and AWS Secret Key) are stored in the secure Sentry gateway rather than within the client applications.
4. Content Level Strong Encryption - Encrypt the data as it is uploaded up to S3 through Sentry, then decrypt the data when the files are downloaded through Sentry.
Prerequisites
Before implementing the sample Sentry policy attached to this article, please first:
- Install Forum Sentry
- Create an Amazon S3 account and obtain AWS Credentials (AWS Access Key Id, AWS Secret Key)
This article assumes the reader has familiarity with the Sentry WebAdmin interface and Amazon S3 API.
Sentry Sample Policy Configuration
Attached to this article is a sample Sentry REST Policy that can be used to securely upload and download files through Sentry to the Amazon S3 cloud storage.
Import
The v8.7 FSG file can be imported into v8.7 or later only. Import this FSG on the System-->Configuration-->Import screen under the GDM Import section. The import password is password.
IMPORTANT NOTE: Prior to importing the FSG, it is strongly recommended that you export your full Sentry configuration (FSX file) on the System-->Configuration-->Export screen.
The FSG will import the REST policy with all dependency policy objects, including:
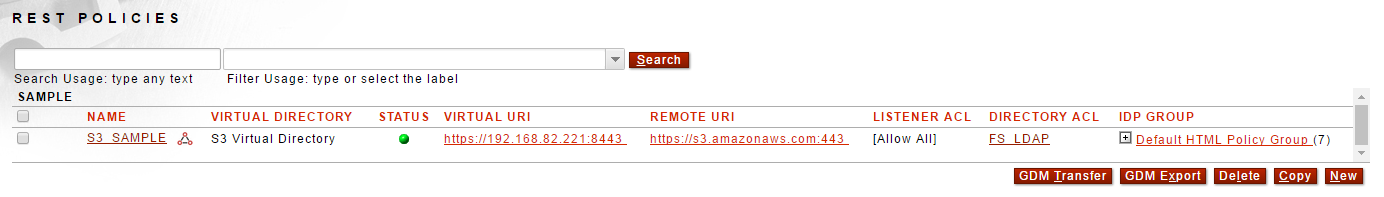
- REST Policy - with "S3" virtual directory that requires Basic Authentication using an LDAP User ACL
- Disabled HTTPS Listener Policy configured for port 8443
- Amazon S3 Remote Policy with invalid credentials
- SSL Termination Policy
- SSL Initiation Policy
- Testing Self-Signed Key Pair used for SSL and Data Encryption
- Encryption Policy
- Decryption Policy
- LDAP Policy for the FS Online LDAP Test Server
- User ACL
figure 1. The Sentry Rest Policy
Configuration Changes
The following Sentry configuration changes are necessary after the import, prior to testing the sample policy:
1. Enable the HTTPS Listener Policy - if there is another policy already using HTTPS/8443 a different port should be used
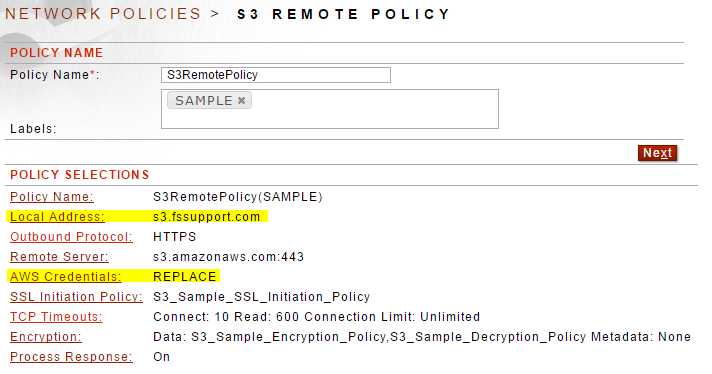
2. Update the Amazon S3 Remote Policy - modify the following:
- Local Address - use your own Sentry DNS name
- AWS Credentials - specify your own AWS Access Key Id and AWS Secret Key
figure 2. The Amazon S3 Network Policy
Testing
Several different clients can be used to test this sample policy. We have included instructions and a sample project for the SOAPSonar API testing tool. Attached is a sample SOAPSonar project file (.ssp) that can be used to upload and download files through Sentry to the S3 API.
Important Testing Notes - To validate the data level encryption happening in Sentry, after you upload a file through Sentry, log into the S3 Management Console and view the contents of the file. The content should be indecipherable as it is encrypted during the upload. The contents will be decrypted by Sentry when the file is later downloaded through Sentry.
It is not necessary to add your AWS credentials with the client request into Sentry. Sentry will automatically build the proper authorization credential needed for the S3 API based on the credentials added to the Amazon S3 policy in Sentry.
Testing with SOAPSonar
Follow the steps below to test the S3 API secured by Sentry using SOAPSonar:
1. Import the attached v8.0.1 SOAPSonar project file (.ssp).
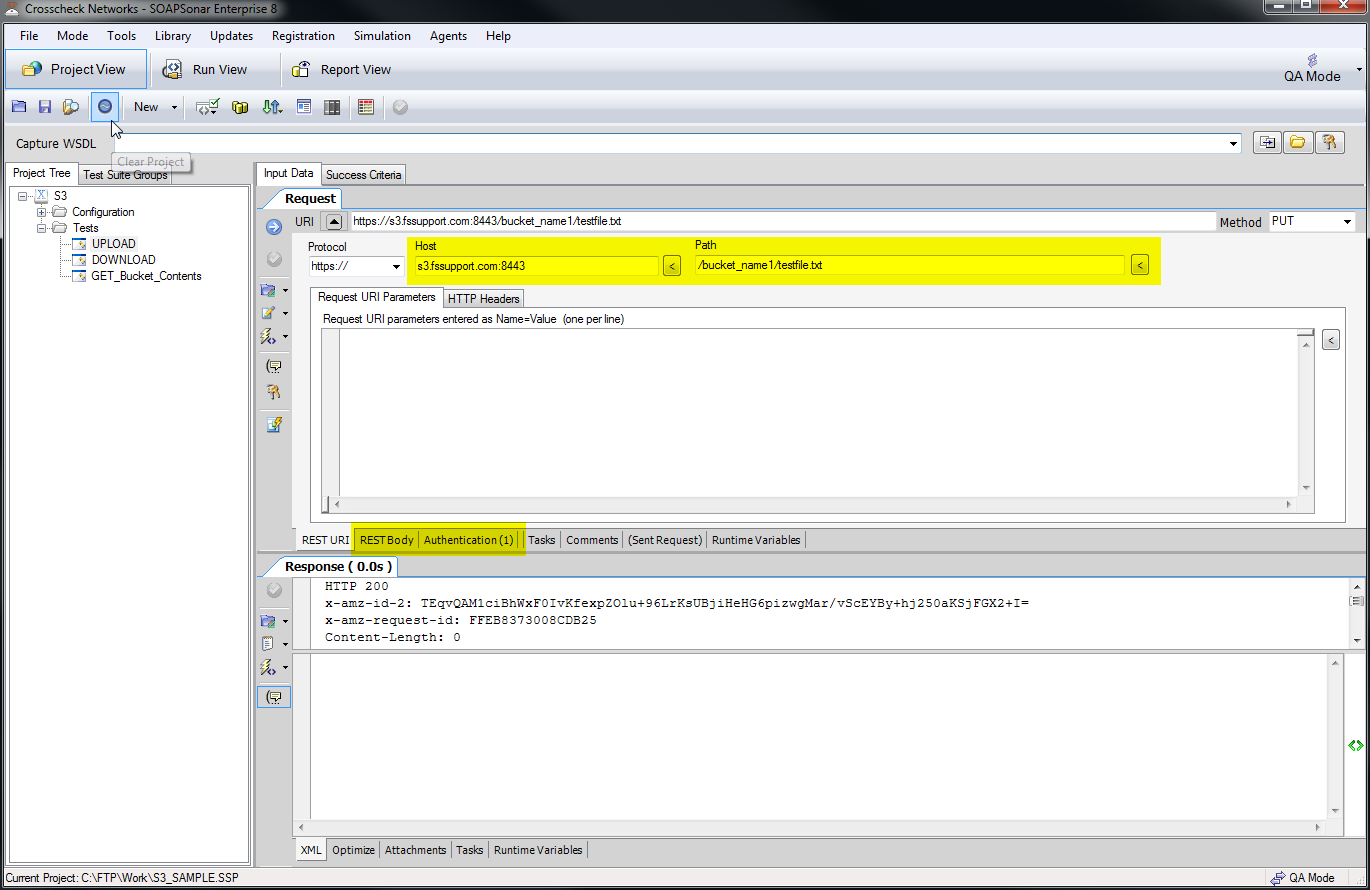
2. Modify each test case (there are 3):
- set the Host field to your Sentry listener IP or DNS name
- set the Path field to your S3 bucket name / file name (e.g. /bucket_name/testfile.txt)
- to change the content of the file, go to the REST Body tab
- to set the user credentials go to the Authentication tab
3. Run test case "Upload" to upload files.
4. Run test case "Download" to download files.
5. Run test case "GET_Bucket_Contents" to retrieve a list of files stored in the bucket.
figure 3. SOAPSonar test cases
User Credential Notes
The LDAP user credentials validated by Sentry are stored in the SOAPSonar test case on the Authentication Tab. If you test with another client application use the LDAP credentials newton/password. If your Sentry instance cannot access the online LDAP server, create a local user in Sentry, add the user to a User Group, and add the User Group to the FS_LDAP User ACL.
Expected Results
Successful upload transactions should return an HTTP 200 OK with no response body. The file stored in S3 should be encrypted.
Successful download transactions should return an HTTP 200 OK with the decrypted file contents in the XML tab.
After each transaction, check the Sentry System log for details of the processing. Be sure to notice the following:
- SSL connections established between SOAPSonar / Sentry and Sentry / S3
- Basic Authentication succeeds using the FS Online LDAP server
- The data is encrypted during the upload
- The data is decrypted during download
Attached is a sample System log extract showing a successful upload transaction.
Conclusion
Forum Sentry v8.7 can be deployed as an API Security Gateway for Amazon S3 cloud storage. The sample policy described in this article illustrates some of the primary benefits of using Sentry as a gateway. This includes secure TLS, identity management with access control, strong content layer encryption, secure storage of the AWS credentials, and secure storage of the keys used to encrypt/decrypt the content being stored in S3.
The secure cloud storage use case can be further extended and/or tightened by using SSL mutual authentication, encrypting the filenames, scanning the content for malware/viruses, etc.
If you have any questions or issues with the sample policy or on this functionality in general, please open a new ticket with Forum Systems Support.

0 Comments