When troubleshooting SAML 2.0 SSO use cases, it is often useful to view the SAML Response generated by the Identity Provider (IdP) and sent to the Service Provider (SP).
For Sentry administrators, this can be very important when trying to configure Forum Sentry as an IdP to generate SAML Responses that match a "known good" sample from a working solution.
The following steps describe how to view the SAML Response from your IdP in your browser using the built-in developer tools with Google Chrome and Mozilla Firefox. Other browsers also have this same capability. The same steps can be used to capture and view a SAML Request.
For both browsers, go to the page where you can reproduce the issue. Then follow the steps below.
Google Chrome
To view a SAML Response in Chrome
These steps were tested using version 7.0.x. The steps should be similar in different versions.
-
Press F12 to open the DevTools.
-
Select the Network tab, and then select Preserve log.
-
Trigger the SAML SSO flow.
-
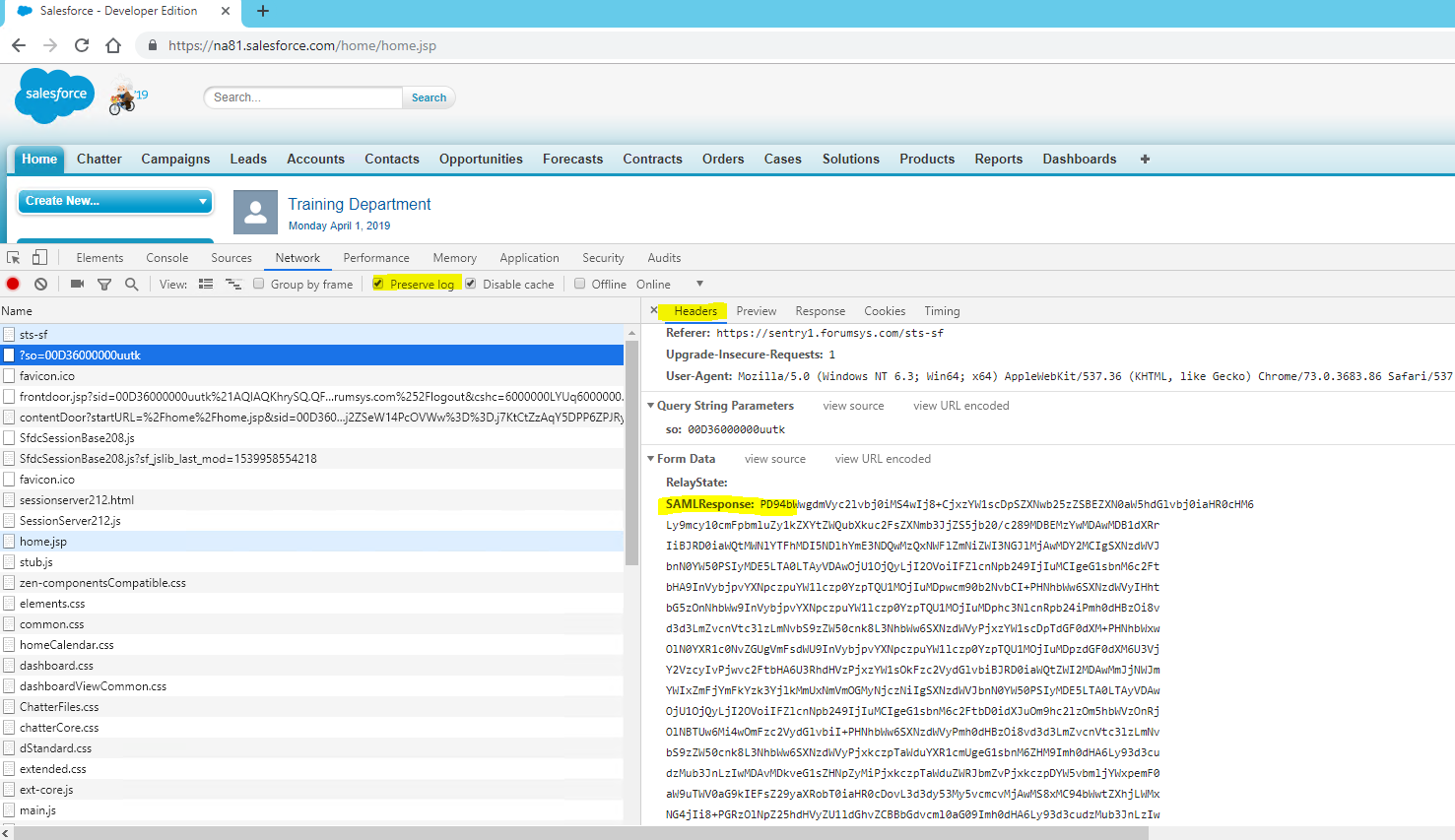
Look for the HTTP POST to the SAML SSO Service Provider endpoint in the developer console pane. This should be the next call after you hit the IdP endpoint. Select that row, and then view the Headers tab at the bottom. Scroll until you see the Form Data section and you should see a SAMLResponse parameter, the value is base64 encoded.
Mozilla Firefox
To view a SAML response in Firefox
This procedure was tested on version 66.0.x of Mozilla Firefox. The steps should be similar in different versions.
-
Press F12 to start the developer tools.
-
Select the Network tab. Enable the Persist Logs option
- Trigger the SAML SSO flow.
-
Look for the HTTP POST to the SAML SSO Service Provider endpoint in the developer console pane. This should be the next call after you hit the IdP endpoint. Select that row, and then view the Params tab. Look for the Form Data section and you should see a SAMLResponse parameter, the value is base64 encoded.

Decoding the Base64 SAML Response
Once you find the base64 encoded SAML Response element in your browser, copy it and use your favorite base-64 decoding tool to extract the XML SAML Response. Notepad++ is one text editor that has a built-in base64 decoding option as well as tools to parse and pretty print XML data.
Remember that SAML Responses may include sensitive information, so be careful using online decoders.
Note that Sentry also has the capability to decode base-64 data via the Convert Value task.
The decoded XML SAML Response XML will be similar to the following:
<?xml version="1.0"?>
<samlp:Response Destination="https://fs-training-dev-ed.my.salesforce.com?so=00D36000000uutk" ID="id-1cea1a02949aba74403415aefcbeb74be2000660" IssueInstant="2019-04-02T00:55:42.269Z" Version="2.0" xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol">
<saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">https://www.forumsys.com/sentry</saml:Issuer>
<samlp:Status>
<samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success"/>
</samlp:Status>
<saml:Assertion ID="id-eb60002bc5bfab1facbadc97b9d2e16ef8c26736" IssueInstant="2019-04-02T00:55:42.269Z" Version="2.0" xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">
<saml:Issuer>https://www.forumsys.com/sentry</saml:Issuer>
<ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:SignedInfo>
<ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>
<ds:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1"/>
<ds:Reference URI="#id-eb60002bc5bfab1facbadc97b9d2e16ef8c26736">
<ds:Transforms>
<ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/>
<ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>
</ds:Transforms>
<ds:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1"/>
<ds:DigestValue>A48Pd57DdK6bR6LrH2Bn6BLMKVE=</ds:DigestValue>
</ds:Reference>
</ds:SignedInfo>
<ds:SignatureValue>
0tfkMJSQAeqLuVnqstye+DoVbagk9FO8kQAiG9+5E3k53ftKgIVHKmZ3kpF6Ir0LBOZ4Mzc8Toaj
zR2diqv8pawy1gXBuCb0S0FfB61jWEWSEsJ+zFrFvB3k8xTE0ILPB0MrQgVSJrkubMbnpv7/RN/Y
zItJmsm8h4Z4PvFXZF4=
</ds:SignatureValue>
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>
MIIChjCCAe+gAwIBAgIBCDANBgkqhkiG9w0BAQUFADBeMQswCQYDVQQGEwJVUzEYMBYGA1UEChMP
VS5TLiBHb3Zlcm5tZW50MQwwCgYDVQQLEwNEb2QxEDAOBgNVBAsTB1Rlc3RpbmcxFTATBgNVBAMT
DENBMi1DUC4wMi4wMTAeFw05OTAxMDExMjAxMDBaFw00ODAxMDExMjAxMDBaMGAxCzAJBgNVBAYT
AlVTMRgwFgYDVQQKEw9VLlMuIEdvdmVybm1lbnQxDDAKBgNVBAsTA0RvRDEQMA4GA1UECxMHVGVz
dGluZzEXMBUGA1UEAxMOVXNlcjEtQ1AuMDIuMDEwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGB
AOzYq2murB5ZjQd4wReI51Lc1F5VwK90OMGRfi71YvwdRjgCudeDXZGW5ayid82y+eTDKFSzo1Li
/BPTUXMpeqHHMCmLeefqxAWmz3aDoilF8IQ53PlejnXJdntsal44w6WdP6ssiXlwzcZDnobAfuDT
PgsnWWfzAkr1/LqEw/QZAgMBAAGjUjBQMA4GA1UdDwEB/wQEAwIF4DAWBgNVHSAEDzANMAsGCWCG
SAFlAwEwATARBgNVHQ4ECgQIP5tVdEyxotcwEwYDVR0jBAwwCoAIoI0mSmDmzZUwDQYJKoZIhvcN
AQEFBQADgYEAkVx9S/20Hir8qMnfMpMGTgMKoVeWoljxim83IkNs1Xqe1oLGHdyDUA66uF8wPkoT
qGrfDYvgBa5Mi0iJREnMWoiWvCe467+L1b2gtvRBMl9bcRj40bvelk0Wn4lBl3VuKXarP5M0PKT5
OWvN2cPLNeXHvV6ZIrC4rmK2ISpIXX4=
</ds:X509Certificate>
<ds:X509Certificate>
MIIClTCCAf6gAwIBAgIBBzANBgkqhkiG9w0BAQUFADBeMQswCQYDVQQGEwJVUzEYMBYGA1UEChMP
VS5TLiBHb3Zlcm5tZW50MQwwCgYDVQQLEwNEb2QxEDAOBgNVBAsTB1Rlc3RpbmcxFTATBgNVBAMT
DENBMS1DUC4wMi4wMTAeFw05OTAxMDExMjAxMDBaFw00ODAxMDExMjAxMDBaMF4xCzAJBgNVBAYT
AlVTMRgwFgYDVQQKEw9VLlMuIEdvdmVybm1lbnQxDDAKBgNVBAsTA0RvZDEQMA4GA1UECxMHVGVz
dGluZzEVMBMGA1UEAxMMQ0EyLUNQLjAyLjAxMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCx
/mIo1Ma/IN8OR7KOjclvIwsv0JFXD/T258DruDZUuGoYiEbAc/ZN7R8OHI7dnv9pBfsvyEl7m2DV
oLZnP0eXJTHjdZxb1TwPHoSIysi9u3xWlPRg+v+GGfKLB9pL0m8SZh97SngerZI14w7vQy0kkXzi
GatSpBoXtWNmsHJNuQIDAQABo2MwYTAPBgNVHRMBAf8EBTADAQH/MA4GA1UdDwEB/wQEAwIBBjAW
BgNVHSAEDzANMAsGCWCGSAFlAwEwATARBgNVHQ4ECgQIoI0mSmDmzZUwEwYDVR0jBAwwCoAINsJc
xaBqdugwDQYJKoZIhvcNAQEFBQADgYEAcfs1pH12Qwdhv4NOJO2xxgMZZo8+A9Zl9c7RxsvuoZOO
yCxoE9wT/lPdUpGoGxtIPoWQs1qXEXnAlXJCXjLCJUHIG1/E6gQUXW0Ty6Ztpc5Dz06pPTN2gt+4
1B3JsL/Klqc4iyCaWr8sYgEPQ8nColWRmIwk9gAasPNkNhyxA3Y=
</ds:X509Certificate>
<ds:X509Certificate>
MIIClTCCAf6gAwIBAgIBBjANBgkqhkiG9w0BAQUFADBeMQswCQYDVQQGEwJVUzEYMBYGA1UEChMP
VS5TLiBHb3Zlcm5tZW50MQwwCgYDVQQLEwNEb0QxEDAOBgNVBAsTB1Rlc3RpbmcxFTATBgNVBAMT
DFRydXN0IEFuY2hvcjAeFw05OTAxMDExMjAxMDBaFw00ODAxMDExMjAxMDBaMF4xCzAJBgNVBAYT
AlVTMRgwFgYDVQQKEw9VLlMuIEdvdmVybm1lbnQxDDAKBgNVBAsTA0RvZDEQMA4GA1UECxMHVGVz
dGluZzEVMBMGA1UEAxMMQ0ExLUNQLjAyLjAxMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC/
lQLtWKzklgYuzhjMiK2CzFmzODsEY/JIVNdn9T8MW4ufpGwnfIV62EUHCFeMYydKBm8Hyjbjrz1o
tINJmrGL5WSAX1/UPtHy1chgXOsFYD6nAHjZAJJGw74nUbKw5+L1wUHU8qXABaaTrRpS1UdKSq4T
CZ18NCjC4Oxcf/yDdQIDAQABo2MwYTAPBgNVHRMBAf8EBTADAQH/MA4GA1UdDwEB/wQEAwIBBjAW
BgNVHSAEDzANMAsGCWCGSAFlAwEwATARBgNVHQ4ECgQINsJcxaBqdugwEwYDVR0jBAwwCoAIq5rr
+cLnVI8wDQYJKoZIhvcNAQEFBQADgYEAOQP3iUX7FtJlL9nvu4F+8o/N5vr+OB28OsbYtW+Q1FzE
fjkUGtT9RiteradpN/xUnS/oj3BfqFtNANkYKrBeqRtm2VeOC3kdCVFnWFME2aoRAQZbWvOwCFc3
yLA7JBdENtDNI54yYHMHPA4/2CuNQq1Iu1ektAS95DIe7ddxL18=
</ds:X509Certificate>
<ds:X509Certificate>
MIICbDCCAdWgAwIBAgIDAYafMA0GCSqGSIb3DQEBBQUAMF4xCzAJBgNVBAYTAlVTMRgwFgYDVQQK
Ew9VLlMuIEdvdmVybm1lbnQxDDAKBgNVBAsTA0RvRDEQMA4GA1UECxMHVGVzdGluZzEVMBMGA1UE
AxMMVHJ1c3QgQW5jaG9yMB4XDTk5MDEwMTEyMDEwMFoXDTQ4MDEwMTEyMDEwMFowXjELMAkGA1UE
BhMCVVMxGDAWBgNVBAoTD1UuUy4gR292ZXJubWVudDEMMAoGA1UECxMDRG9EMRAwDgYDVQQLEwdU
ZXN0aW5nMRUwEwYDVQQDEwxUcnVzdCBBbmNob3IwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGB
ANPzucEztz+nJ/ZBHVyceZ2q0pUQt4TO2qPlWAw+TotWvz6qIS1QE/7zGS56yxHP89O4X1efnZeA
rx2VVxLfNNS9865N53ymINQETtpjYT49Ko03z8U8yfn68DlIBHi9sN31JEYzoUafF58Eu883lAwT
Q6qQrJF4HbrzGIQqgitHAgMBAAGjODA2MBEGA1UdDgQKBAirmuv5wudUjzAMBgNVHRMEBTADAQH/
MBMGA1UdIwQMMAqACKua6/nC51SPMA0GCSqGSIb3DQEBBQUAA4GBABZWD2Gsh4tP62QSG8OFWUpo
4TulIcFZLpGsaP4T/2Nt7lXUoIJMN7wWjqkmYf5/Rvo4HxNcimq3EkeYcrm1VoDueJUYGvRjcCY5
mxkghI27Yl/fLKE9/BvQOrvYzBs2EqKrrT7m4VK0dRMR7CeVpmPP08z0Tti6uK2tzBplp1pF
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</ds:Signature>
<saml:Subject>
<saml:NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified">training</saml:NameID>
<saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
<saml:SubjectConfirmationData NotOnOrAfter="2019-04-02T00:56:42.269Z" Recipient="https://fs-training-dev-ed.my.salesforce.com?so=00D36000000uutk"/>
</saml:SubjectConfirmation>
</saml:Subject>
<saml:Conditions NotBefore="2019-04-02T00:55:42.269Z" NotOnOrAfter="2019-04-02T00:56:42.269Z">
<saml:AudienceRestriction>
<saml:Audience>https://www.forumsys.com/sentry</saml:Audience>
</saml:AudienceRestriction>
</saml:Conditions>
<saml:AuthnStatement AuthnInstant="2019-04-02T00:55:42.269Z">
<saml:AuthnContext>
<saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:unspecified</saml:AuthnContextClassRef>
</saml:AuthnContext>
</saml:AuthnStatement>
<saml:AttributeStatement xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<saml:Attribute Name="sf_user" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic">
<saml:AttributeValue xsi:type="xsd:string">training@forumsys.com</saml:AttributeValue>
</saml:Attribute>
</saml:AttributeStatement>
</saml:Assertion>
</samlp:Response>

0 Comments