Introduction
Okta provides various identity management services. The one that interests us in this scenario is Okta as a SAML Identity Provider (IdP). When Okta is being used as a SAML IdP solution, Forum Sentry can easily integrate to make use of this service. In this case Forum Sentry plays the role of resource protection and serve as the SAML Service Provider (SP).
Configure Okta as SAML IdP
The setup requires an existing Okta account with admin privileges. Depending on the Okta SAML IdP setup, Forum Sentry is flexible to conform where more attributes and other items are used besides what’s covered below.
Configuring Okta as SAML IdP involves adding an application. The following link to Okta provides detailed steps to add the SAML application:
Setting Up a SAML Application in Okta
Setup
Login to Okta with Admin privileged account
Note: Depending on the layout you have configured the following steps might not all look alike but the general idea is the same. Here is a sample setup to add an application that will serve as a SAML IdP.
Click Admin
Click Applications
Click Add Application
Click Create New Application
Select SAML 2.0 then click Create
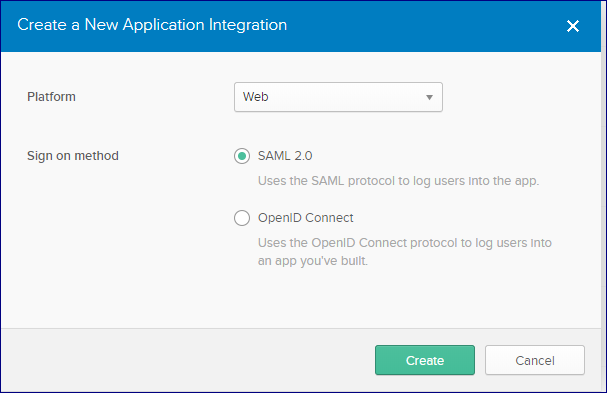
Name your application then click Next
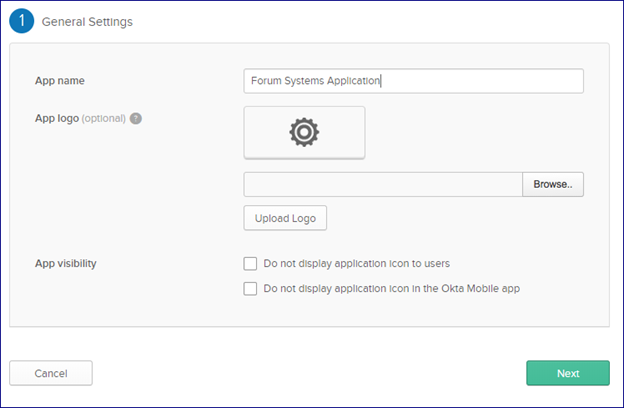
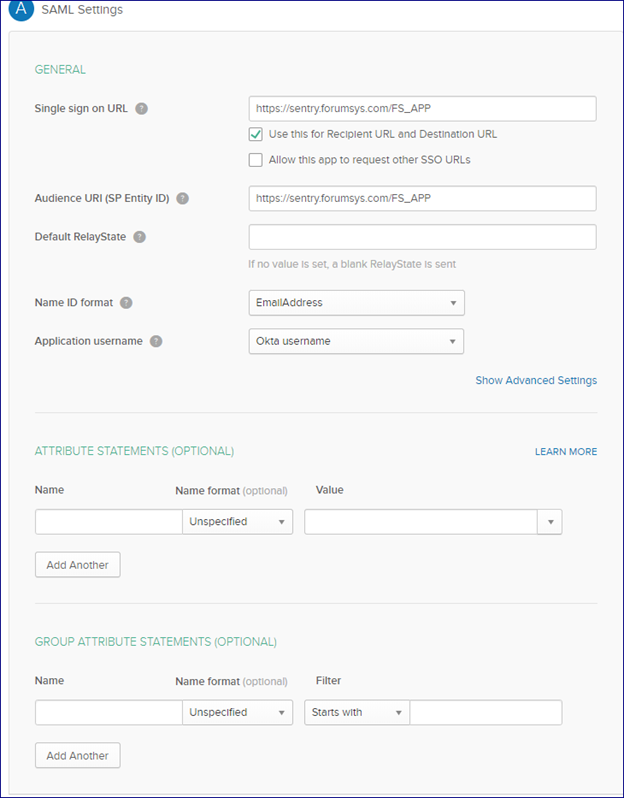
Fill in the information specific to your application
Before proceeding further there is an option to preview the setup to make sure it matches the intent of your use case:
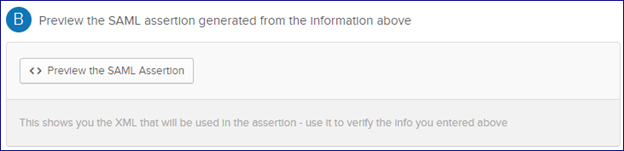
Click Next
Select appropriate items for your application then click Finish
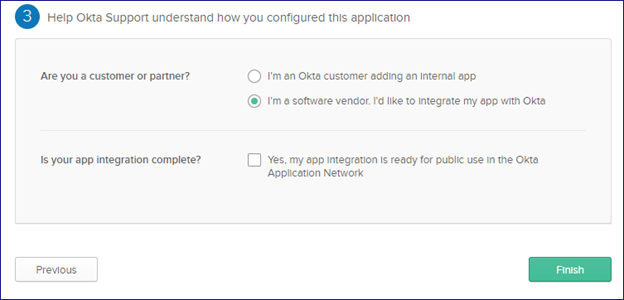
You can now view your application setup and are able to make changes:
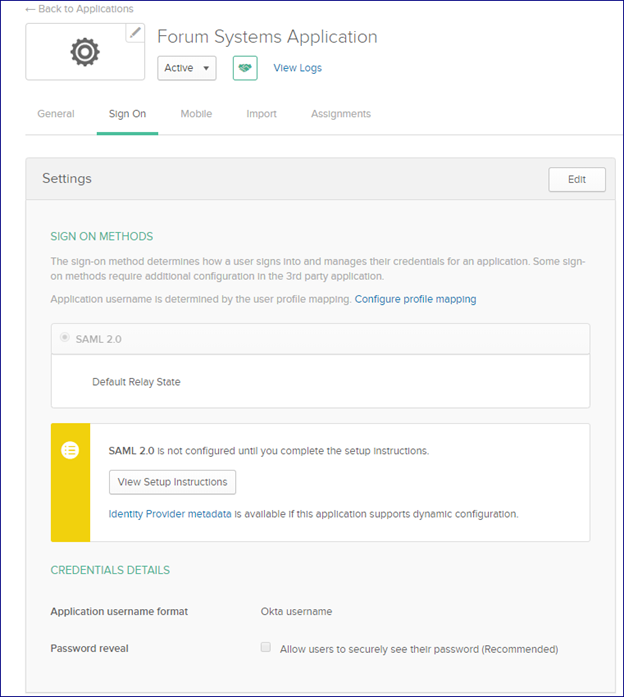
You can click the link to view the Okta SAML IdP metadata or View Setup Instructions to collect information that will be needed for the Forum Sentry SP setup. The minimum items needed are
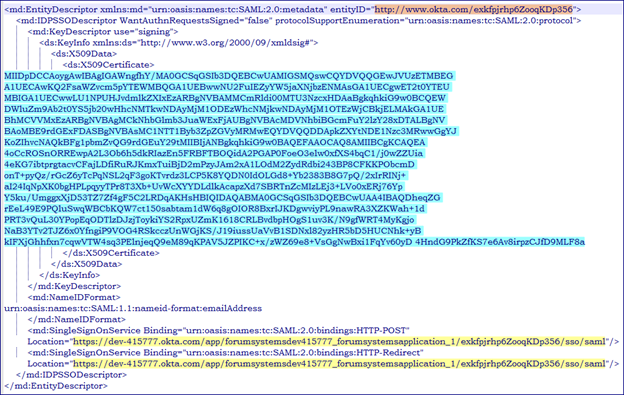
- Identity Provider Single Sign-On URL
- Identity Provider Issuer
- X.509 Certificate
The items listed above are highlighted in the metadata file:
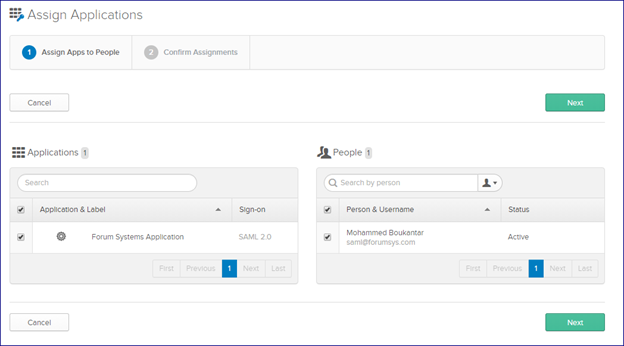
You can now assign your application by clicking on Assignments then confirming:
Configure Forum Sentry as SAML SP to Okta SAML IdP
Attached below is the v8.9 Forum Sentry FSG (import password is password) of a sample HTML policy. The HTML policy allows access to https://www.forumsys.com/homepage upon SAML response validation.
HTML Policy

UIDAC Task
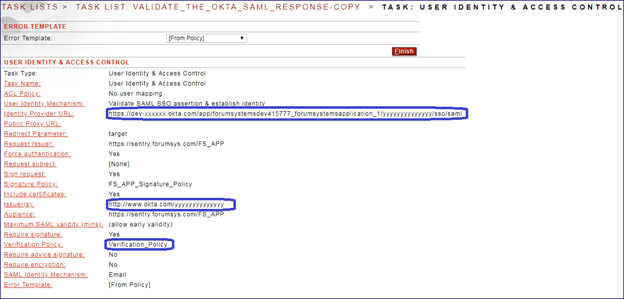
The highlighted items in the User Identity and Access Control Task (UIDAC) are items mentioned above and collected from the IdP. The verification policy is using the X.509 certificate supplied by the IdP and should be configured prior to the UIDAC task.
Testing
Use a browser to test this use case.
For debugging purposes, enable the Developer Tools in your browser and then go to Network and check Preserve log on your browser. More info on tracing SAML 2.0.
1. Send a request to your Sentry HTML policy (the SP endpoint in this SAML SSO flow).
2. The HTML policy then redirects you to the login page on Okta (the IdP).
3. Authenticate to Okta
4. Upon successful authentication you are redirected back to your HTML policy which validates the SAML and allows access to the protected resource.
Request to HTML Policy which redirects to Okta:
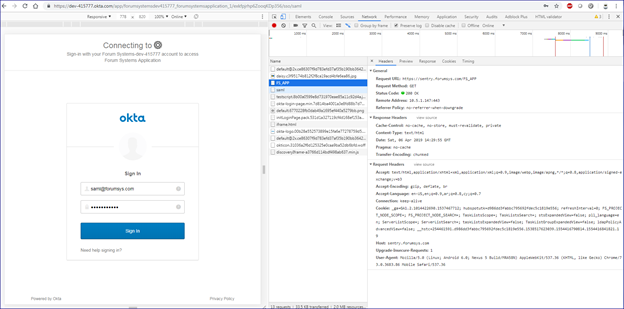
Request to Okta showing the signed SAML request:
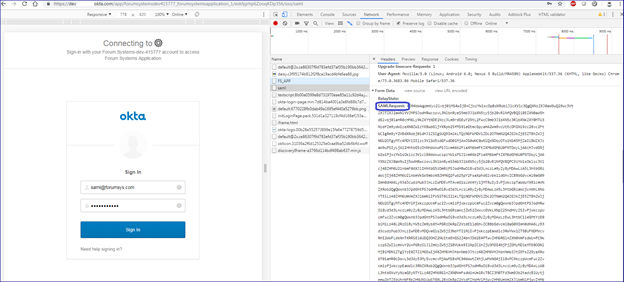
Automatic redirection back to the Sentry HTML policy with SAML response and access to the protected resource:
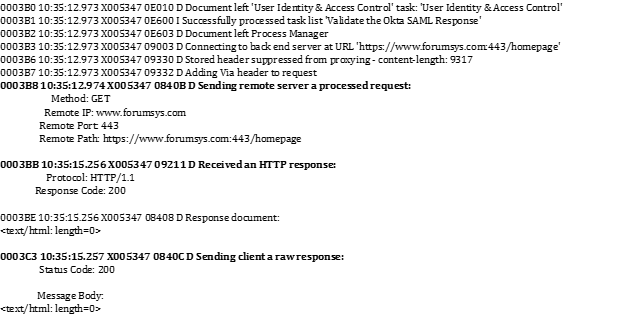
Forum Sentry System Log
The following is an example of Sentry system log entries for this use case:



0 Comments