Introduction
Forum Sentry is often used as a reverse proxy / gateway for web sites and portals. Sentry administrators might want to seamlessly force clients (e.g. web browsers or mobile apps) to use HTTPS without having any errors returned if the clients use HTTP.
This article includes a sample Sentry task list (FSG) that will redirect clients using HTTP to the same URL only changing the protocol to HTTPS.
For example, a client using the URL:
http://server1.fssupport.net/test/resource?query1=test
will be redirected to:
https://server1.fssupport.net/test/resource?query1=test
Note that this a sample solution only, there are multiple ways to solve similar use cases. If this example doesn't satisfy your use case requirement please contact Forum Systems Support for assistance.
The Sample Task List
The attached sample task list first captures the original URL details from the HTTP request and then redirects to the same URL only changing the protocol to HTTPS. This works with and without query parameters in the URL.
Notes:
1. The import password is password.
2. The FSG is from Sentry v8.9 and will import into v8.9 and later.
More information each task in the task list is below.
Figure 1. The HTTP to HTTPS Task List
Map Attributes and Headers Task
This task breaks up the HTTP URL (Full Request URL) into template attributes. Templates utilize known patterns to map dynamic information to user attributes. In this case we are creating two template attributes, one for the hostname part of the URL and another for everything following the first / after the hostname.
Templates use curly brackets/braces. You can name the templates whatever you want, in the sample they are "server" and "path".
For example, given our example URL above as a Source:
http://server1.fssupport.net/test/resource?query1=test
Using the following Target Name:
Creates two template attributes:
server = server1.fssupport.net
path = test/resource?query1=test
Figure 2. The Map Attributes and Headers Task
Redirect Task
The second task in the task list will redirect the client to a new location by returning a 300 level status code with an HTTP Location header.
You can specify whatever Redirect Code you want to use.
The Redirect task supports static and dynamic sources. In this case we want the source to be Template, as we'll be using the Template attributes mapped in the first task.
In the Source Name field we'll use a combination of static data with the dynamic Template attributes.
For our sample use case we'll specify:
Using our example URL above, this will set the value of the HTTP Location header to:
https://server1.fssupport.net/test/resource?query1=test
Note the only difference from the original is the protocol changed from HTTP to HTTPS.
Figure 3. The Redirect Task
Applying the Task List
The HTTP to HTTPS task list should be associated to any HTTP virtual directory in Sentry that you want to redirect to an HTTPS virtual directory.
For example, if you have an HTML policy for a web portal and you want to ensure the client's only uses HTTPS, your virtual directories for the portal will all use HTTPS listener policies.
You can add an HTTP listener policy in "service mode" - meaning there is no back-end or remote policy specified - to this HTML policy and associate the this redirect task list to that virtual directory.
Figure 4. Sample HTML Policy for an HTTPS Web Portal
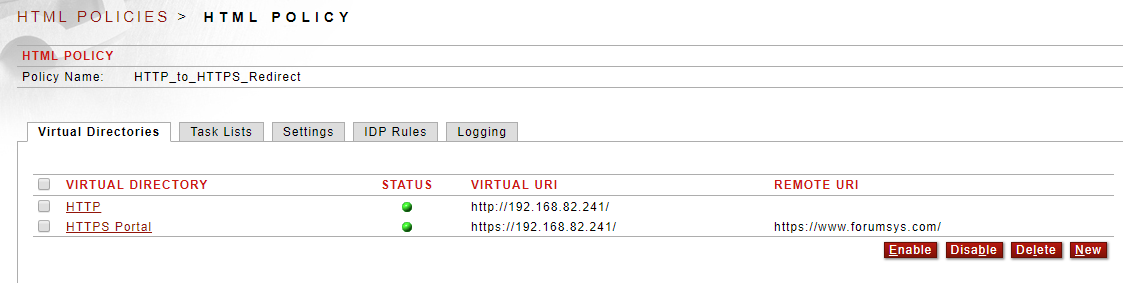
Figure 5. The HTTP to HTTPS task list is associated to the HTTP virtual directory which is in "service mode"
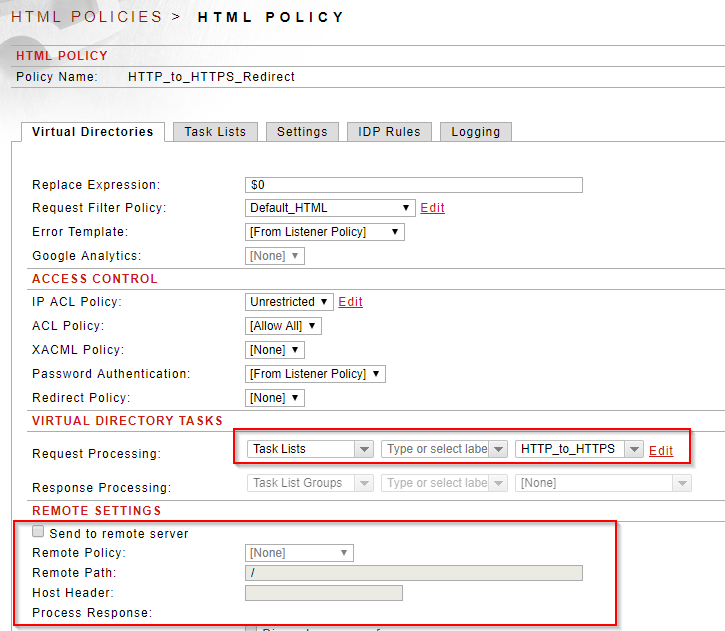
Sentry Logs
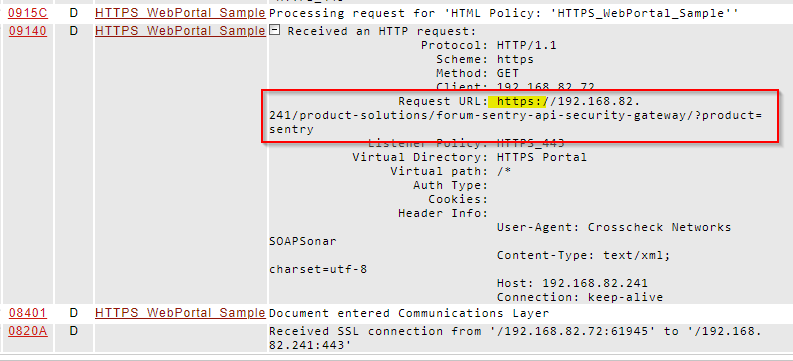
The log entries below show an example of this sample task list redirecting a client from HTTP to HTTPS.
Figure 6. Sentry Access log showing the two transactions
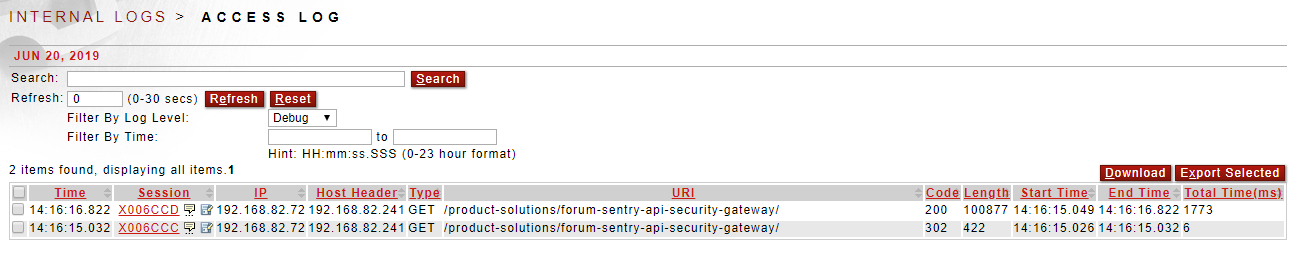
Figure 7. The first HTTP transaction, notice the redirect sent back to the client
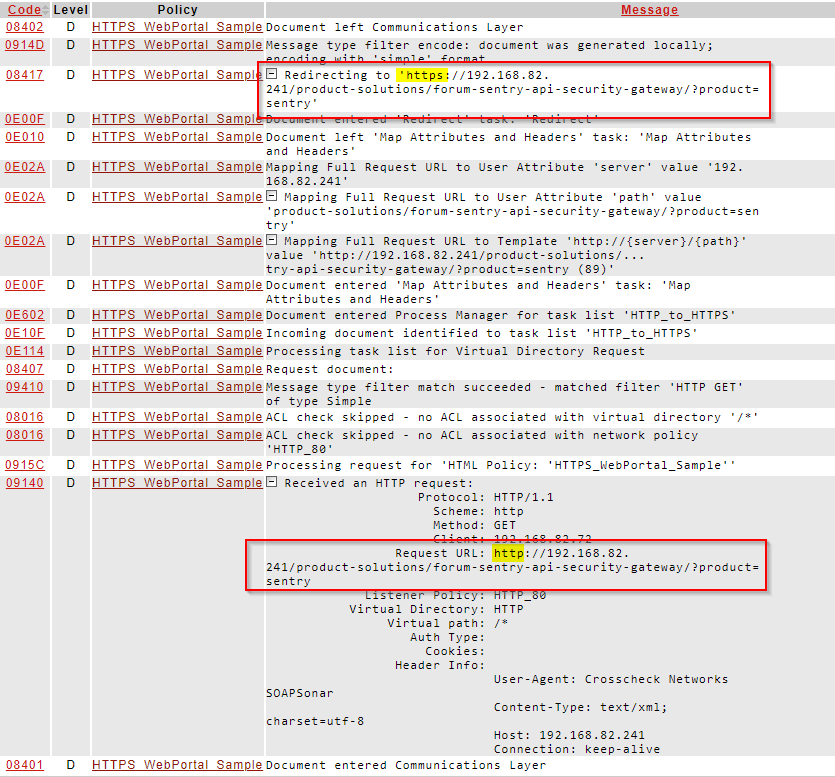
Figure 8. The HTTPS transaction which is a result of the redirect

0 Comments