With Sentry v9.1.x the OAuth IdP Policies now support token revocation.
Each Sentry OAuth IdP policy will have a specific virtual directory for revocation calls. The token revocation functionality in Sentry adheres to the OAuth 2.0 Token Revocation RFC7009 and includes revocation of bearer (access) and refresh tokens. Tokens persisted in a database are also removed upon revocation.
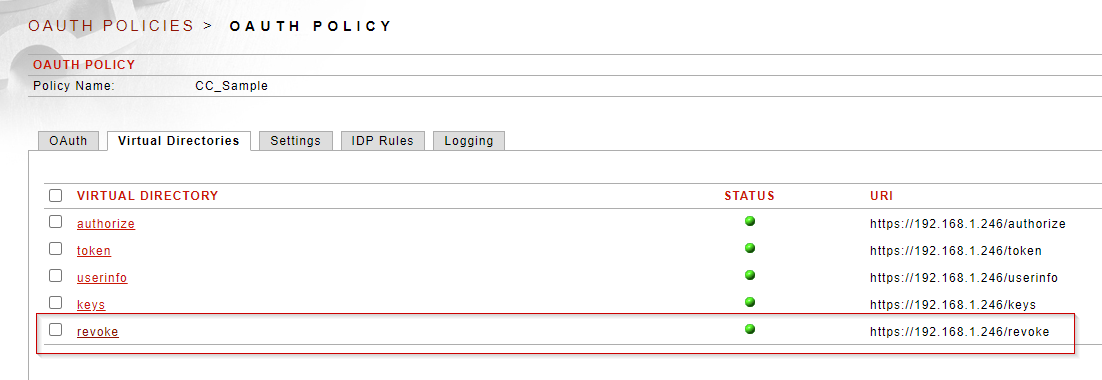
The client passes the token to be revoked into the /revoke endpoint in Sentry with a URL encoded form post:
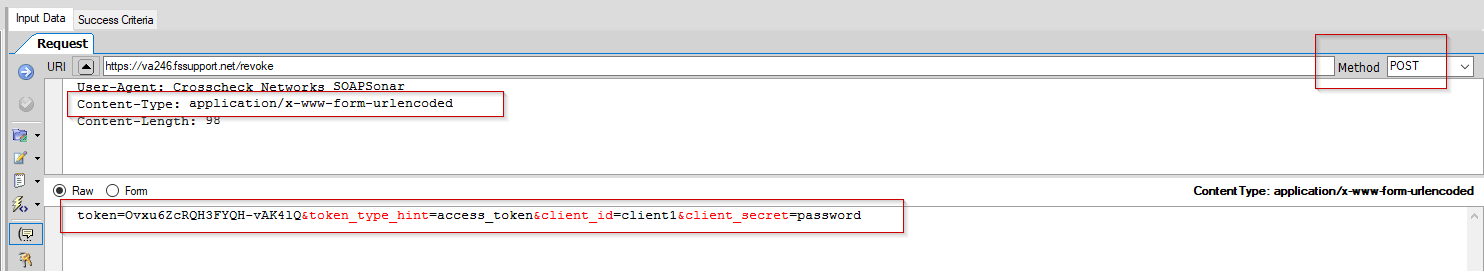
Sentry returns a 200 OK upon revocation and removes the token from any storage locations (local cache and database if using persistence).
The attached Sentry system log shows several transactions to a REST policy and OAuth policy in Sentry. The highlights are:
- Token retrieval (via client credentials grant type).
- An API call to a Sentry REST Policy which requires token validation to access a weather API.
- Token revocation call.
- A second API call to the weather API with the same token, this time it fails because the token was revoked.
The image below shows the Sentry access log for the scenario outlined above. The attached system log has more info on each transaction.
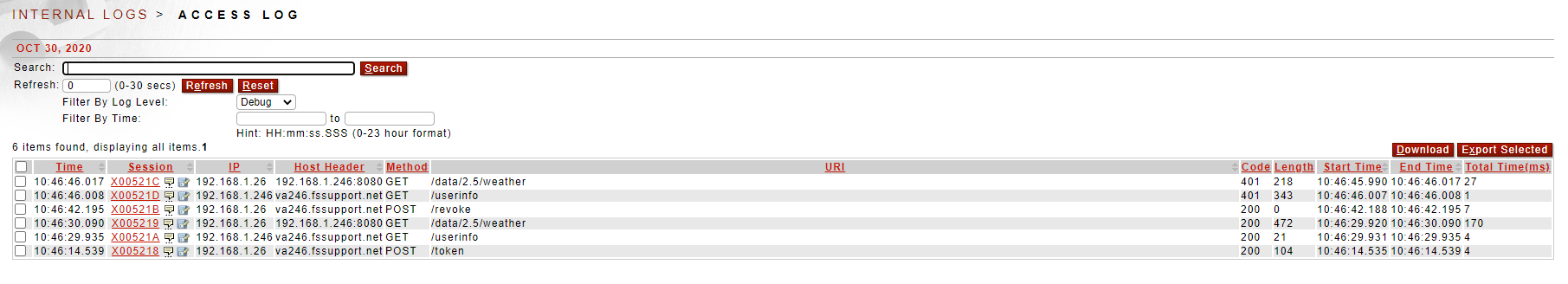
X005218 – client calls the OAuth policy /token to get the token
X005219 – client calls the REST policy /data/2.5/weather to get the Weather API using the access token
X00521A – REST policy calls the OAuth policy /userinfo to validate the token
X00521B – client calls the OAuth policy /revoke to revoke the token
X00521C – client calls the Weather API again with the same access token (results in a 401)
X00521D – REST policy calls the OAuth policy /userinfo to validate the token (results in a 401) - this happens prior to the client receiving the 401 from the previous transaction
If you have any questions on how Sentry processes OAuth token revocation, please contact Forum Systems Support.

0 Comments